User interface and functionalities of LeoConfidential.
User interface and functionalities of LeoConfidential, software for encryption-decryption Unicode text with state of art proprietary algorithm.LeoConfidential - the software application with self-explanatory user interface for encryption -decryption of Unicode text.
Screenshot: 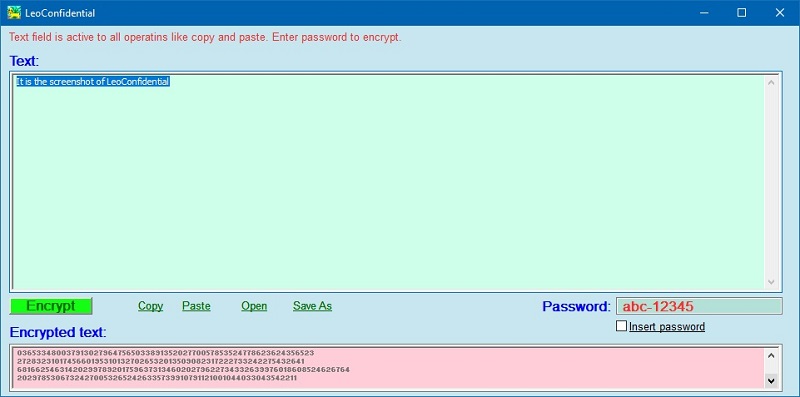
Following operations are available:
By clicking inside "Text" of "Encrypted text" edit control user makes one of them active for following operations:
Copying its whole content in clipboard;
Pasting inside with complete replacement of previous content the content of clipboard.
Open text file content.
Saving content of edit box in text file.
User can drag text file into one of these two edit boxes.
User can type content of the message inside "Text" edit box in one or more languages installed on its computer in the same time.
If "Text" edit control is active user can encrypt it into "Encrypted text" control by clicking on "Encrypt" button and then use encrypted content to save in file or paste into the e-mail message for example.
The Password must fit security conditions like length and number of distinct letters. Password can be multi-languages as well.
If "Encrypted text" control is active its content will be decrypted by clicking "Decrypt" button (the same button for encryption procedure just change caption and functionality). The Password of course must be the same as used for encryption.
User has option to incorporate Password inside encrypted text or not. There are advantages and disadvantages for both options.
If Password incorporated in the encrypted message can be restored by developers for some nominal handling fee. We will also positively respond to any legal request from law protection officials.
If user will chose not to incorporate Password into the encrypted text we have no easy methods to decrypt document and in most cases the information will be lost irreversibly with the password forever. We cannot guarantee impossibilities of deciphering by third parties because believe into limitless of human creativity. What we are saying that we have no idea how to do it in any imaginable way.
Note that even very small editing encrypted text could (or not) corrupt it content fully or partially depend on luck.